
The moment enterprises quietly crossed
Most organizations began with AI in “assistant mode”: summarize, search, draft, explain.
Then the workflow changed.

Suddenly, agents were no longer producing text. They were approving requests, updating records, triggering workflows, creating tickets, calling tools, and moving work forward—sometimes faster than humans could reliably notice. That’s where the failure pattern changes.
In the agent era, risk is rarely a single “model mistake.” It’s systemic: too many agents, unclear ownership, shared credentials, untracked tool permissions, invisible spend, and no reliable way to stop runaway automation.
This is why Gartner’s June 2025 prediction landed so sharply: over 40% of agentic AI projects may be canceled by the end of 2027 due to escalating costs, unclear business value, or inadequate risk controls. (Gartner)
The winners won’t be the teams with “more agents.”
They’ll be the teams with a real operating discipline for agents.
And one foundational building block sits at the center of that discipline:

What is an Enterprise Agent Registry?
An Enterprise Agent Registry is the system of record for every AI agent that can take actions in your environment.
Think of it as the agent equivalent of what enterprises already built for other critical assets:
- IAM for user identities
- CMDB for infrastructure and service dependencies
- API gateways for controlling external access
- Service catalogs for standardizing consumption
- GRC systems for evidence and audit trails
The Agent Registry plays the same role for autonomy:
If an agent can act, it must be registered. If it’s not registered, it’s not allowed to act.
The registry answers the executive questions that always show up in production:
- What agents exist right now?
- Who owns each agent?
- What systems can it access?
- What actions can it take—and under what conditions?
- What did it do (with evidence), and who approved it?
- What does it cost per day/week/month?
- How do we pause or kill it instantly if something goes wrong?
Without a registry, enterprises end up with shadow autonomy: agents that behave like production software—but are governed like experiments.

Why “Agent Registry” is not just rebranded IAM
Traditional IAM was built for humans and static services. Agents are different in ways that matter operationally and legally.
1) Agents are dynamic
They can be cloned, reconfigured, and redeployed quickly. What looks like “one agent” can become twelve variants by the time audit asks questions.
2) Agents are compositional
One agent calls tools that call other tools, and soon you have a chain of delegated actions. In practice, that means risk moves through graphs, not steps.
3) Agents can be tricked into unsafe actions
Prompt injection and tool-output manipulation aren’t theoretical. OWASP’s LLM guidance highlights prompt injection and insecure output handling as top risks, and the GenAI Security Project has also emphasized “excessive agency” patterns—where systems do more than they should. (OWASP Foundation)
4) Agents can be expensive by accident
A subtle loop can create cost explosions: repeated tool calls, retries, long chains, “just one more attempt.” Costs rise quietly—until finance notices.
5) Agents create “action risk,” not just “information risk”
A chatbot hallucination is embarrassing. An agent hallucination that triggers a workflow can become an incident.
So yes—agents need identity.
But they also need ownership, policy-based action gating, operational controls, and financial guardrails.
That is what an Agent Registry provides.
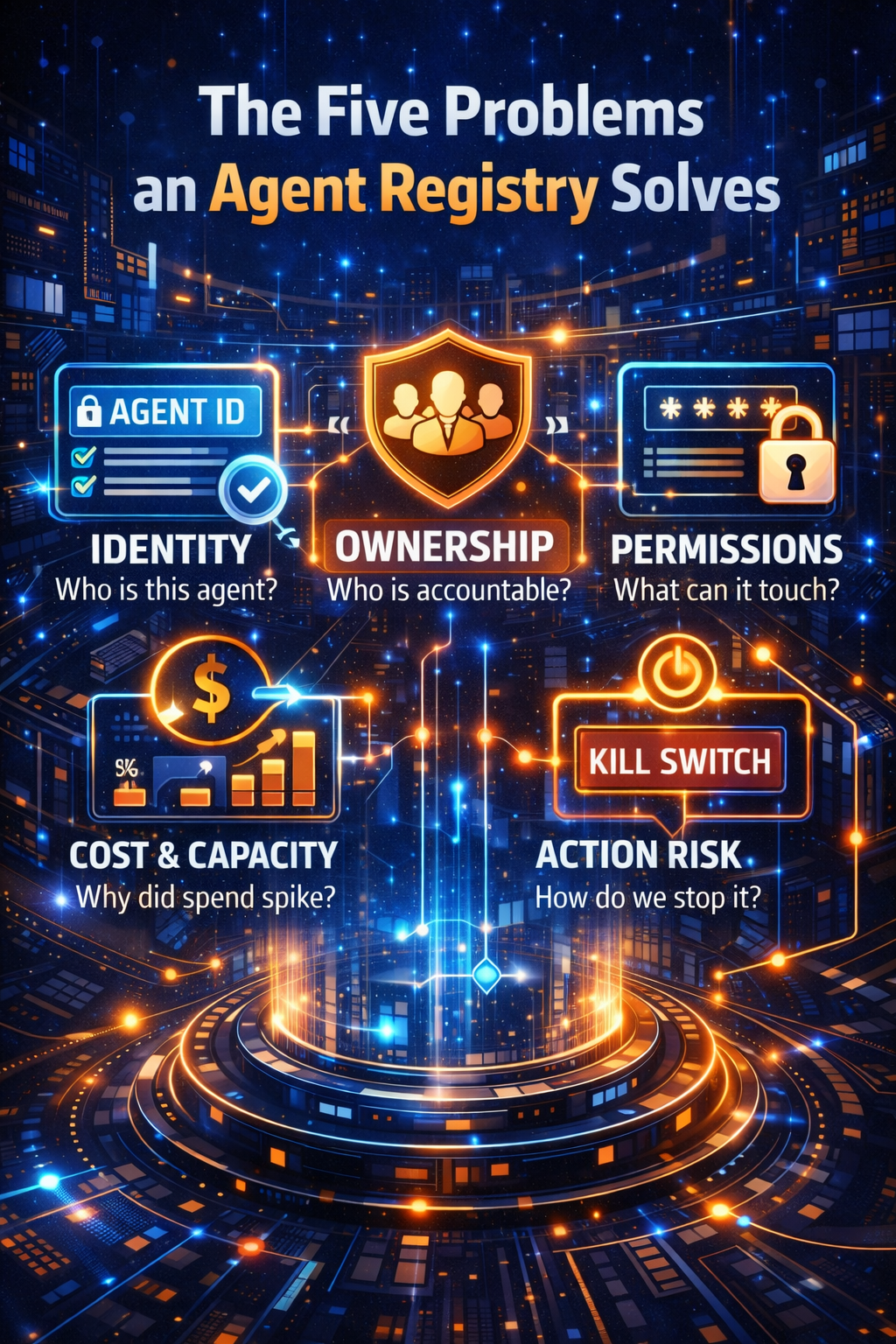
The five problems an Agent Registry solves
1) Identity: “Who is this agent, really?”
Every agent should have a unique, verifiable identity—separate from human accounts and shared service credentials.
A registry makes identity concrete through practical elements:
- Agent ID (stable identifier)
- Environment scope (dev/test/prod)
- Runtime identity (how it authenticates to tools)
- Trust tier (what it is allowed to do)
- Deployment lineage (what shipped, by whom, from which pipeline)
This aligns with Zero Trust’s core idea: trust is not assumed; access is evaluated continuously and enforced through policy. (NIST Publications)
Simple example:
An “Access Approval Agent” should never operate using a generic admin key. The registry forces it to use its own identity—and restricts it to the exact approvals it’s permitted to recommend or execute.
2) Ownership: “Who is accountable when it acts?”
Agents fail in the most boring way possible: nobody owns them.
A registry makes ownership explicit:
- Business owner (who benefits)
- Technical owner (who maintains)
- Risk owner (who accepts residual risk)
- On-call escalation path (who responds)
- Change authority (who can upgrade it)
This maps cleanly to what governance frameworks insist on: accountability, roles, and clear responsibility structures. NIST’s AI Risk Management Framework emphasizes governance as a cross-cutting function across the AI lifecycle. (NIST Publications)
Simple example:
A “Procurement Triage Agent” routes purchase requests. When it misroutes one, the registry prevents the two-week scavenger hunt: “Who built this?” “Who approved it?” “Who owns the risk?”
3) Permissions: “What can it touch—and what can it do?”
Permissions for agents must be more granular than role-based access—because agents operate in context, and context changes.
Your registry should bind an agent to constraints like:
- Allowed systems (specific tools/APIs only)
- Allowed actions (read/write/approve/execute)
- Data boundaries (what it can see, store, and share)
- Escalation thresholds (when it must route to a human)
- Safety policies (what it must refuse)
- Rate limits (to prevent loops and abuse)
This is least privilege, made operational. (NIST Publications)
Simple example:
An “HR Onboarding Agent” can create tickets and draft emails, but cannot directly provision privileged access without an approval path—ideally “human-by-exception,” not “human-in-every-loop.”
4) Cost & capacity: “Why did spend spike overnight?”
Agentic systems introduce a new spend pattern:
- LLM usage (tokens, context size, reasoning mode)
- Tool calls
- Retries
- External APIs
- Long-running workflows
- Multi-agent cascades
Without an Agent Registry, finance and engineering see the bill—but can’t attribute cost to:
- a specific agent
- a specific workflow
- a specific business unit
A registry turns cost into a managed control:
- budget per agent
- per-action caps
- throttling and circuit breakers
- anomaly alerts
- downgrade paths (cheaper models/tools under pressure)
Simple example:
A “Customer Resolution Agent” gets stuck on a hard case and starts looping—tool calls escalate, the model re-asks itself, retries multiply. The registry enforces a budget cap and forces escalation rather than letting spend silently spiral.
5) Kill switch: “How do we stop it—now?”
Every agent needs a safe stop path that is:
- immediate
- auditable
- reversible (where possible)
- consistent across environments
This is not only about emergencies. It’s also for:
- incident response
- compliance holds
- suspected prompt injection
- degraded data quality
- vendor outages
- unexpected behavior changes
If you can’t stop an agent quickly, you don’t have autonomy—you have uncontrolled automation.
And uncontrolled automation is exactly how agentic pilots become “cancellation candidates.” (Gartner)
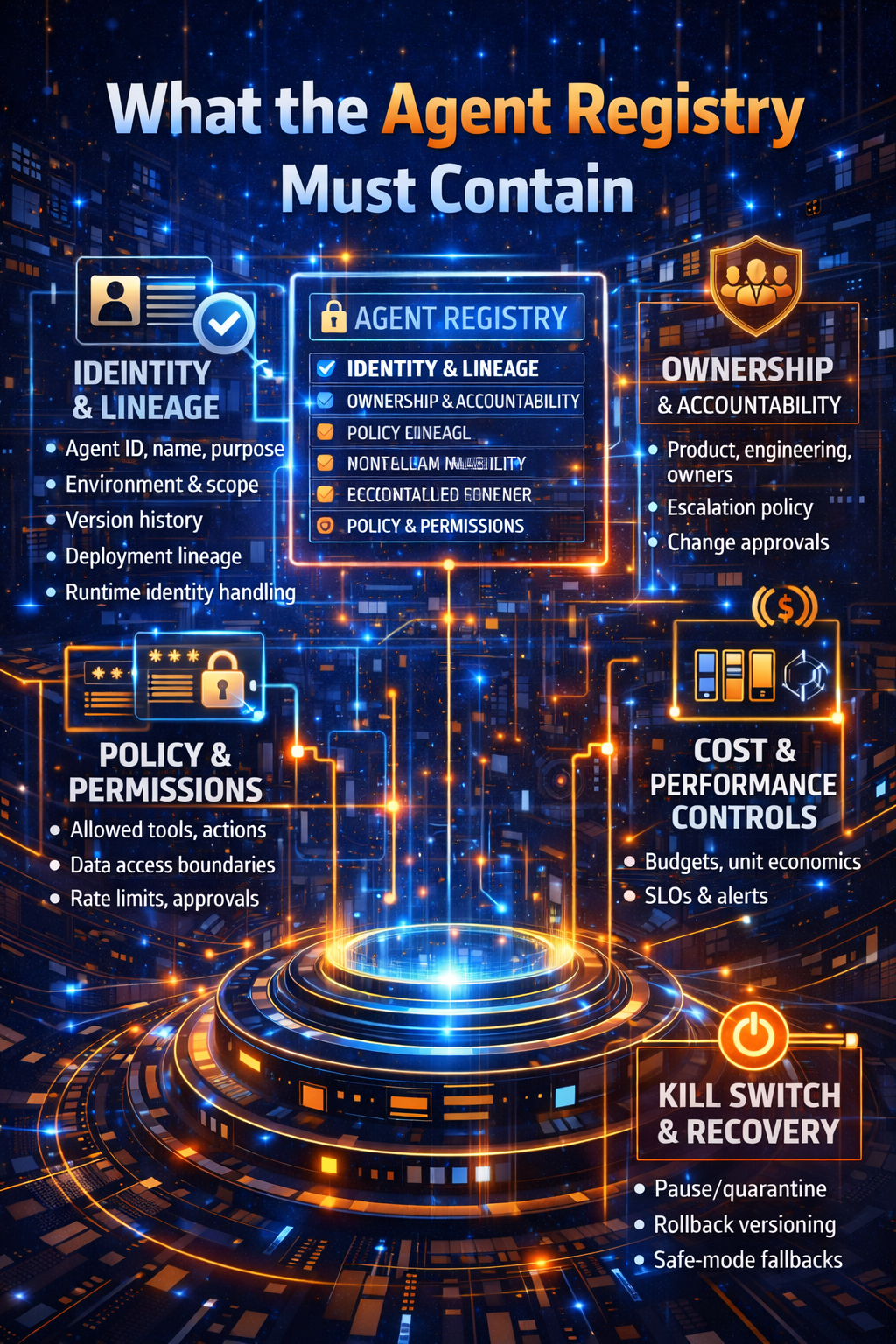
What the Agent Registry must contain
You don’t need a fancy buzzword stack. You need a durable record with enforcement hooks.
At minimum, every registered agent should include:
-
A) Identity and lineage
- Agent ID, name, purpose
- Environment and scope
- Version history
- Deployment lineage (what shipped, from where)
- Runtime identity and secrets-handling approach
-
B) Ownership and accountability
- Product owner, engineering owner, risk owner
- Escalation policy
- Change approval path
-
C) Policy and permissions
- Allowed tools/APIs
- Allowed actions and constraints
- Data access boundaries
- Required approvals by risk level
- Rate limits and throttles
-
D) Observability and evidence
- Action logs (what it did)
- Evidence trail (why it did it; inputs/outputs captured safely)
- Approval evidence for high-risk steps
- Incident correlations
-
E) Cost and performance controls
- Budget caps
- Cost per outcome (unit economics)
- Reliability targets (SLOs) and alert thresholds
-
F) Kill switch and recovery
- Pause/disable capability
- Quarantine mode (read-only)
- Rollback versioning
- Safe-mode fallbacks
This structure maps to what mature risk programs want: governance, accountability, monitoring, and controlled access—principles also reinforced in the NIST AI RMF and Zero Trust architectures. (NIST Publications)
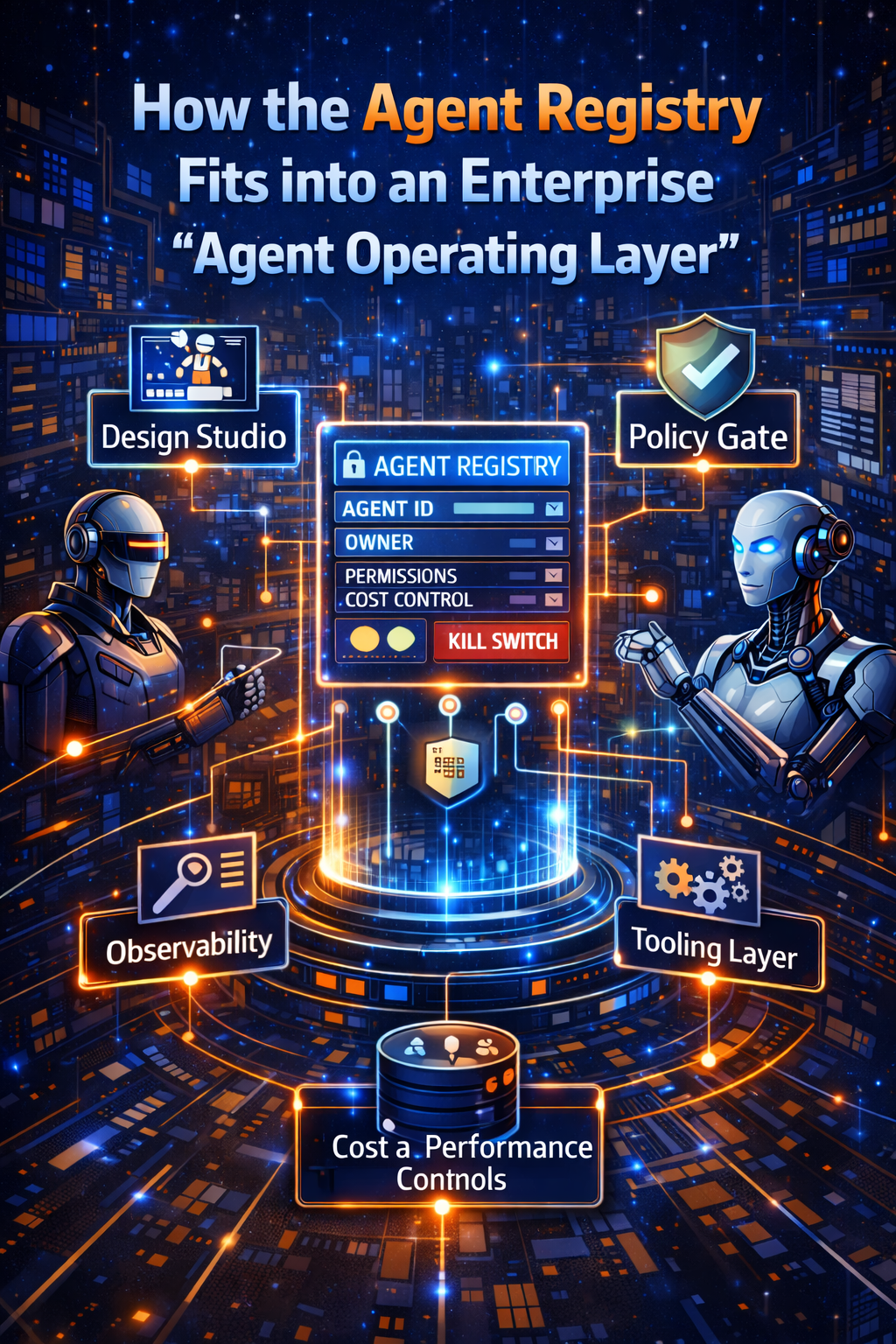
How the Agent Registry fits into an enterprise “agent operating layer”
If you already think in terms of:
- service catalogs
- control planes
- governed autonomy
- design studios
…then the Agent Registry becomes the missing spine that connects them.
A simple mental model:
- Design Studio creates agents safely
- Agent Registry certifies and governs their existence
- Policy Gate enforces permissions and approvals
- Tooling Layer executes actions through constrained interfaces
- Observability records evidence and outcomes
- Catalog publishes approved agents as reusable services

Why the registry becomes a strategic advantage
This is the part executives care about.
Speed increases when control increases
It sounds counterintuitive, but it’s how real enterprises work.
When autonomy is governable, teams deploy faster because:
- approvals are standardized
- audits are automated
- incidents are containable
- spend is predictable
- rollouts are repeatable

The registry turns “agent sprawl” into “managed autonomy”
If you don’t build it, you’ll still get agents. You just won’t know where they are, what they can do, or what they cost.
And the moment a high-visibility incident hits—prompt injection, data leakage, unsafe action, runaway spend—leadership will do the simplest thing:
freeze deployments.
The registry prevents that organizational whiplash by making autonomy operable.

Implementation: a rollout that doesn’t slow the business
Phase 1: Register before you restrict
- Stand up a minimal registry
- Require registration for any production agent
- Start with identity + ownership + purpose + tool list
- Observe first; don’t block everything
Phase 2: Bind permissions to the registry
- Put tool/API access behind policy gates
- Enforce “no registry, no runtime credentials”
- Add rate limits, budgets, approval tiers
Phase 3: Make evidence default
- Standardize action logs
- Capture approvals
- Store inputs/outputs safely (with retention rules)
- Connect to incident response and audit workflows
Phase 4: Add automated controls
- Quarantine on anomaly
- Auto-disable on policy violations
- Auto-downgrade on cost spikes
- Roll back to last-known-good versions
This mirrors how mature organizations adopt Zero Trust: map first, then enforce incrementally and consistently. (NIST Publications)
Executive takeaway: the question to ask next week
If you’re a CIO/CTO/CISO, ask this in your next leadership meeting:
“Can we list every agent that can take action in production—its owner, its permissions, its cost, and how to stop it in 60 seconds?”
If the answer is “not really,” you don’t have an agent strategy yet.
You have experiments.
And experiments don’t scale.
Glossary
- Agentic AI: AI systems that can plan and take actions via tools/APIs to keep a process moving, not just generate outputs. (Thomson Reuters)
- System of record: The authoritative source the enterprise trusts for “what exists” and “what is true.”
- Kill switch: A standardized mechanism to pause/disable an agent immediately and safely.
- Least privilege: Granting only the minimum access needed to perform an approved action. (NIST Publications)
- Prompt injection: Input crafted to manipulate a model or agent into unsafe behavior—especially dangerous when the agent has tool access. (OWASP Foundation)
- Excessive agency: When an AI system is given more autonomy/permissions than it can safely handle, increasing the chance of harmful actions. (OWASP Gen AI Security Project)
- Enterprise Agent Registry: The authoritative system of record that governs AI agents’ identity, ownership, permissions, cost, auditability, and shutdown.
Enterprise Agent Registry – Frequently Asked Questions
Doesn’t IAM already solve this?
IAM solves identity and access for humans and services. Agents need additional controls: ownership, policy-based action gating, cost caps, evidence trails, and kill-switch operations.
Is the registry only for security teams?
No. It’s a business scaling mechanism. It prevents program shutdowns by making cost, accountability, and operational risk manageable.
Do we need this if agents are “read-only”?
If an agent truly cannot act (no tool calls, no writes), registry requirements can be lighter. The moment it can trigger actions—even indirectly—registration becomes essential.
What’s the first step?
Require every production agent to register with owner, purpose, environment, and tool list—then progressively bind credentials, permissions, and logging to the registry.

Conclusion: autonomy is a production capability, not a demo feature
Enterprises didn’t scale APIs by hoping developers “behave.” They scaled APIs by building gateways, catalogs, and governance.
Agents will be no different.
If autonomy is your future, the Enterprise Agent Registry is the first system you should build—because it’s the simplest way to make agents identifiable, accountable, constrained, observable, and stoppable.
In the coming years, the competitive advantage won’t come from having more agents.
It will come from having agents you can run like an enterprise.
References and further reading
- Gartner press release (June 25, 2025): prediction on agentic AI project cancellations by 2027. (Gartner)
- OWASP Top 10 for Large Language Model Applications (Prompt Injection, Insecure Output Handling, etc.). (OWASP Foundation)
- OWASP GenAI Security Project: “Excessive Agency” risk. (OWASP Gen AI Security Project)
- NIST AI Risk Management Framework (AI RMF 1.0). (NIST Publications)
- NIST SP 800-207: Zero Trust Architecture (least privilege, policy enforcement). (NIST Publications)
- Thomson Reuters: explanation of agentic AI vs generative AI (useful definitions). (Thomson Reuters)
- Service Catalog of Intelligence: How Enterprises Scale AI Beyond Pilots With Managed Autonomy – Raktim Singh
- The AI SRE Moment: Why Agentic Enterprises Need Predictive Observability, Self-Healing, and Human-by-Exception – Raktim Singh
- The Agentic Identity Moment: Why Enterprise AI Must Treat Agents as Governed Machine Identities | by RAKTIM SINGH | Dec, 2025 | Medium
- The AI SRE Moment: How Enterprises Operate Autonomous AI Safely at Scale | by RAKTIM SINGH | Dec, 2025 | Medium

Raktim Singh is an AI and deep-tech strategist, TEDx speaker, and author focused on helping enterprises navigate the next era of intelligent systems. With experience spanning AI, fintech, quantum computing, and digital transformation, he simplifies complex technology for leaders and builds frameworks that drive responsible, scalable adoption.
