The System of Record for Autonomous AI Identities (and the missing layer behind safe scale)
An Enterprise AI Agent Registry is the authoritative system of record that defines, governs, and tracks autonomous AI agents—covering their identity, ownership, permissions, tools, lifecycle state, and audit evidence. Without an agent registry, enterprises cannot safely operate or scale AI systems that take real-world actions.
Enterprises won’t lose control because AI is too intelligent.
They’ll lose control because autonomous agents exist without identity, ownership, or revocation.What Is Enterprise AI? A 2026 Definition for Leaders Running AI in Production – Raktim Singh

The production truth: once AI can act, it becomes an “actor”
In early enterprise AI, you could get away with thinking in terms of models and prompts. The AI suggested things. Humans decided.
But as soon as an AI system can take actions—create a ticket, approve a request, change a record, trigger a workflow, send an email, grant access, update a payment status—your enterprise doesn’t just have “AI.”
It has a new kind of actor operating inside real business systems.
And every enterprise that has ever run critical systems knows the first question to ask about any actor is not “How smart is it?” It’s:
- Who is it?
- Who owns it?
- What is it allowed to do?
- Where is it running?
- How do we revoke it instantly if it misbehaves?
- How do we prove what it did, and why?
That is why the Enterprise AI Agent Registry is becoming non-negotiable.
Not because it is trendy.
Because it’s the only way autonomy becomes governable.

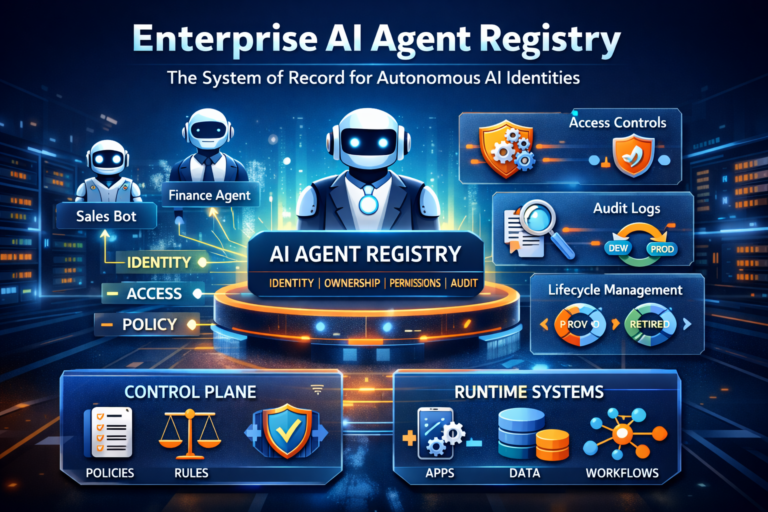
What is an Enterprise AI Agent Registry?
An Enterprise AI Agent Registry is the authoritative system of record for every AI agent that can act inside your environment.
It is a governed registry where each agent is recorded with:
- a unique identity
- a business owner and technical owner
- the agent’s purpose and decision scope
- the tools and systems it can access
- permissions (read vs write vs execute)
- the policy bundle that constrains it
- its runtime location (where it actually runs)
- its lifecycle state (sandbox → pilot → production → retired)
- links to logs, traces, decision records, evaluations, incidents
If you want a simple analogy:
IAM is how you govern humans and services.
The Agent Registry is how you govern autonomous actors.
This aligns with global governance thinking that risk management starts with mapping and inventorying AI systems across the lifecycle (a core emphasis in NIST’s AI Risk Management Framework). (NIST Publications)

Why prompts and “policy documents” are not enough
Why prompts and “policy documents” are not enough
Most enterprises initially try to govern agents with:
- prompt rules (“never do X”)
- written policies
- a Confluence page listing “approved assistants”
- a spreadsheet of pilots
These fail for the same reason “security awareness training” fails as a primary control:
it is not enforceable.
Agents operate at machine speed, across tools, with emergent behavior under new context. That’s why security communities now explicitly highlight tool misuse, prompt injection, excessive permissions, and unintended data exposure as core risks when deploying LLM-based applications and agentic systems. (OWASP)
So the enterprise needs something more fundamental:
A system that makes an agent real in the eyes of operations, security, audit, and leadership.
That system is the Agent Registry.

The mental model that makes this obvious: agents need passports, not prompts
A prompt is like instructions you give a contractor.
But critical systems don’t run on “instructions.” They run on:
- identity
- permissions
- audit trails
- revocation
- lifecycle controls
So treat agents like this:
- Passport (Identity): Who is the agent?
- Visa (Permissions): What systems can it enter and what can it do there?
- License (Scope): What decisions and actions is it allowed to take?
- Flight recorder (Evidence): What did it do, when, and under what context?
- Border control (Revocation): How do we stop it instantly?
That’s what the Agent Registry operationalizes.

What the Agent Registry is not (avoid the common confusion)
An Enterprise AI Agent Registry is not:
- a model registry (models are components; agents are actors)
- a prompt library
- a chatbot directory
- an observability dashboard (though it links to observability)
- IAM itself (though it integrates deeply with IAM)
It is the bridge between your governance intent (Control Plane) and where actions happen (Runtime).
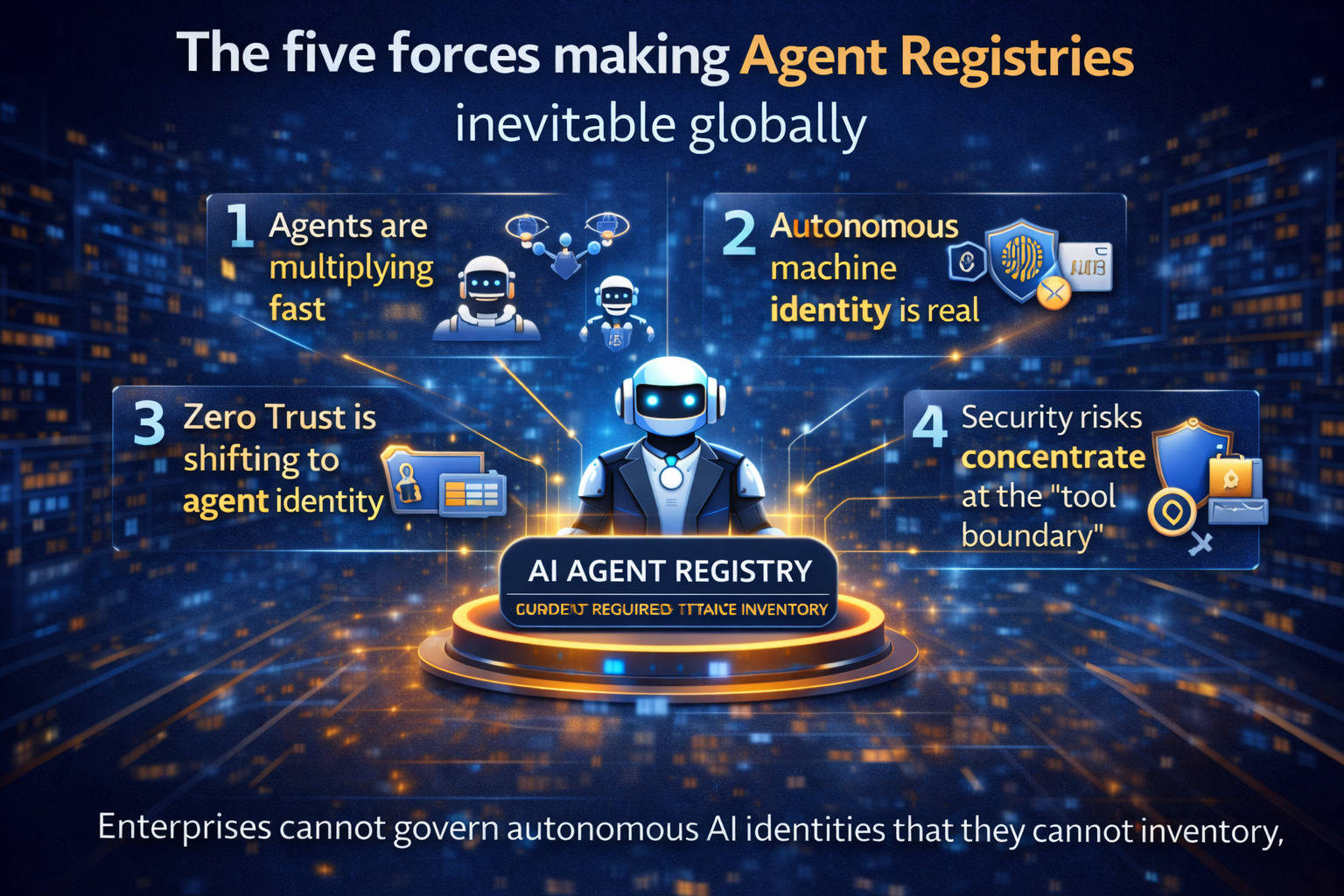
The five forces making Agent Registries inevitable globally
The five forces making Agent Registries inevitable globally
1) Agents are multiplying faster than enterprises can track
Teams can spin up agents like microservices. Vendors can embed agents into products. Orchestrators make it easy to create “agent swarms.”
Without a registry, you get what every CIO fears:
“We don’t know what’s running.”
2) Agents require a new identity class: “autonomous machine identity”
Identity leaders are already moving here. Microsoft, for example, explicitly describes agent identities as a distinct identity model for autonomous agents (special service principals) designed for auditable token acquisition and governance. (Microsoft Learn)
That’s a signal: the market is standardizing “agent identity” as a real concept, not a metaphor.
3) Zero Trust is shifting from network → workload identity → agent identity
In modern distributed systems, identity is increasingly assigned to workloads using standards like SPIFFE/SPIRE (cryptographically verifiable workload identities). (Spiffe)
Agents are simply the next step: workload identity for services, agent identity for autonomous actors.
4) Security risks concentrate at the “tool boundary”
OWASP’s GenAI security work highlights how LLM-based apps and agentic systems introduce new risk classes (prompt injection, sensitive data disclosure, tool misuse, etc.). (OWASP)
Where do those risks become real?
Not inside the model.
At the point the agent can call tools and take actions.
That’s why the registry must declare and constrain tool access.
5) Auditability requires an authoritative record of “what exists”
You cannot govern what you cannot enumerate. That’s why NIST’s AI RMF emphasizes structured risk management across the lifecycle, beginning with mapping what systems exist, what they do, and how they are used. (NIST Publications)
A registry is how “inventory” becomes operational, not theoretical.
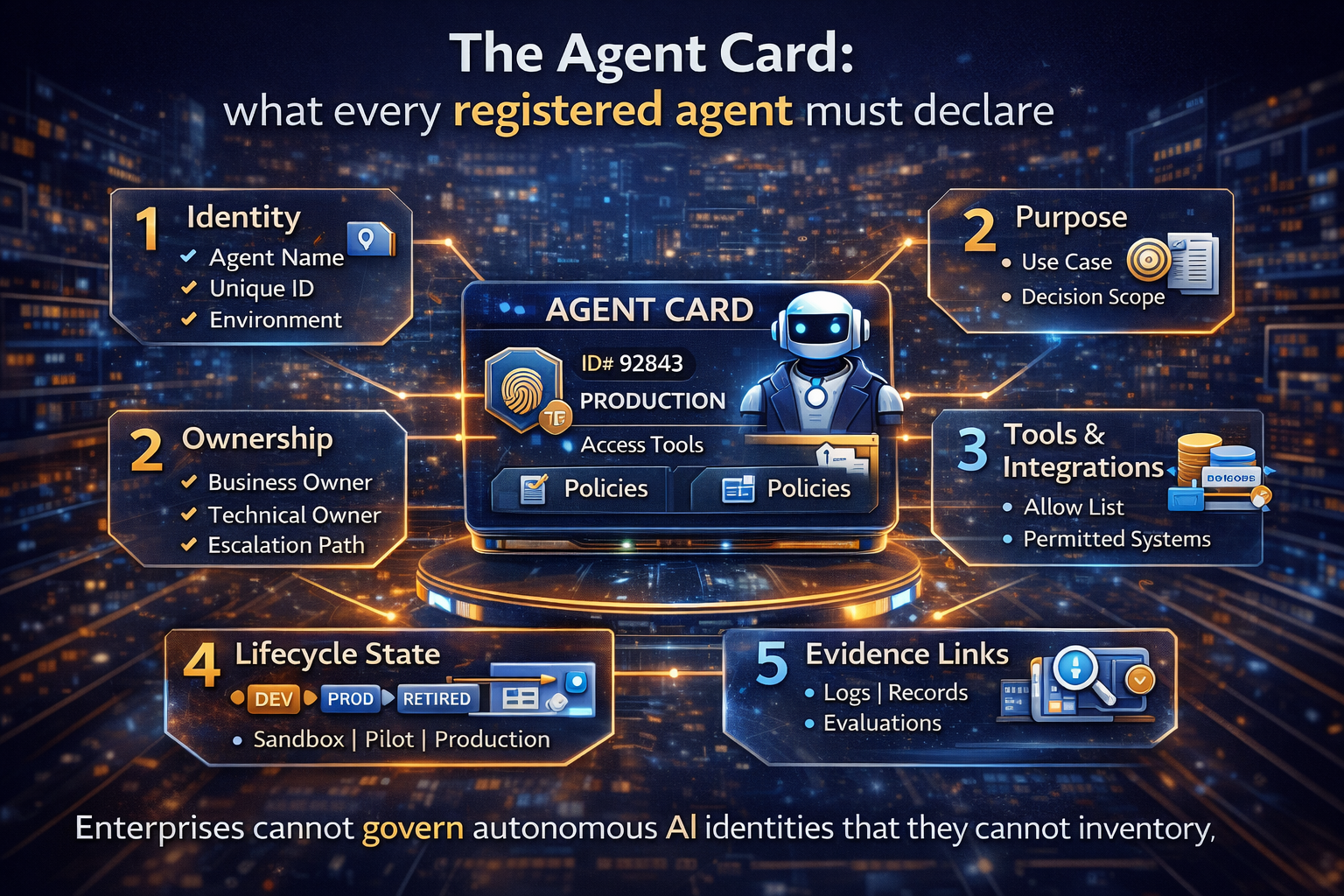
The Agent Card: what every registered agent must declare
To make this work at scale, every agent needs a standardized “Agent Card” in the registry. Keep it readable, but complete.
1) Identity
- Agent name (stable)
- Unique ID (immutable)
- Environment scope (dev/test/prod)
- Identity mechanism (agent identity / workload identity mapping)
2) Ownership (accountability is the point)
- Business owner (accountable for outcomes and risk)
- Technical owner (build/operate responsibility)
- On-call/escalation path
- Cost center / funding tag
3) Purpose and decision scope
- What it is for (in one sentence)
- Allowed decision types (advice-only, actioning, irreversible)
- What it must never do
- Human oversight mode (approval required / exception-based / autonomous under limits)
4) Tools and integrations (the real risk surface)
- Tool allow-list (APIs, systems, connectors)
- Data sources it can read
- Systems it can write to
- Rate limits and quotas
- “High-risk tool” flags (identity, payments, entitlements)
5) Policy bundle
- Which policies apply (security, compliance, operational)
- Required evidence outputs (logs, decision records)
- Required guardrails (content filters, tool constraints)
6) Lifecycle state
- Sandbox / pilot / production
- Last risk review date
- Expiry / re-certification date
- Deprecation plan
This is how an agent stops being a “cool demo” and becomes a governable system.
Three simple examples (so it’s easy to feel the difference)
Example 1: The “Ticket Triage Agent”
Without a registry:
Someone deploys an agent that reads incoming support tickets and posts “recommended actions” into a shared channel. It gradually starts updating tickets directly because “it’s faster.” No one notices permission creep.
With a registry:
The agent is registered as:
- read-only in production ticketing fields
- allowed to create drafts, not final updates
- rate-limited
- linked to an owner and on-call rotation
If behavior changes, the agent’s identity can be revoked immediately.
Example 2: The “Procurement Assistant Agent”
It compares vendors, drafts a purchase request, and submits it.
Registry rule that prevents a scandal:
The agent is explicitly forbidden from:
- creating vendors
- changing payment details
- approving purchases
It can draft and route, but approvals remain role-bound.
Example 3: The “Access Provisioning Agent”
It checks eligibility and provisions access.
This is where registries pay for themselves.
If an access agent runs under a shared service account, it becomes untraceable. If it over-provisions, you will struggle to prove what happened.
With a registry:
- the agent has a distinct identity
- permissions are least-privilege
- every provisioning action is linked to evidence and policy context
- you can revoke identity instantly (hard stop)
This is the difference between “automation” and “governed autonomy.”
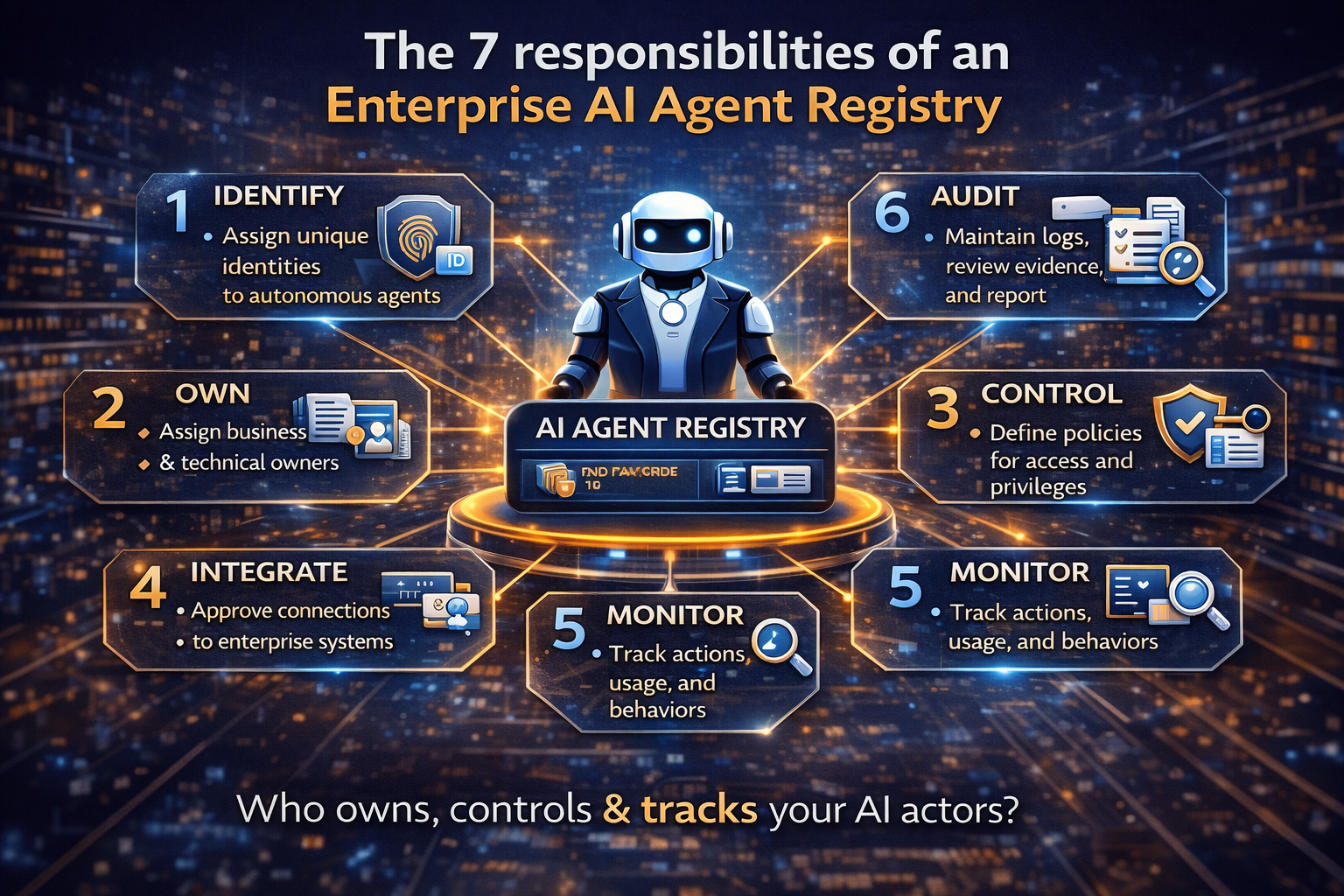
The 7 responsibilities of an Enterprise AI Agent Registry
1) Discovery: “what agents exist?”
The registry must capture agents from:
- internal platforms
- orchestrators
- vendor systems
- shadow deployments discovered through monitoring
2) Identity: “who is this agent?”
This is where agent identities become real. Industry identity systems are already formalizing agent identity patterns for autonomous agents. (Microsoft Learn)
3) Permissions: “what is it allowed to do?”
The registry defines least-privilege boundaries and tracks permission changes over time.
4) Tool boundary control: “what tools can it call?”
This directly reduces OWASP-class risks related to tool misuse and unintended actions. (OWASP)
5) Lifecycle governance: “is it production-worthy today?”
Agents should not run forever without review. Registry-driven expiry and re-certification prevent “zombie autonomy.”
6) Evidence linkage: “can we prove behavior?”
Registry links to:
- runtime logs and traces
- decision records
- evaluations
- incident reports
This turns audits into retrieval, not investigation.
7) Revocation: “can we stop it now?”
You need two kinds of stops:
- soft stop: pause execution
- hard stop: revoke identity / block tool access
This is where zero trust identity thinking (workload identity patterns like SPIFFE) becomes operationally valuable. (Spiffe)
How Agent Registry fits in the Enterprise AI Operating Model The Enterprise AI Operating Model: How organizations design, govern, and scale intelligence safely – Raktim Singh
In one line:
Control Plane governs the rules. Enterprise AI Control Plane: The Canonical Framework for Governing Decisions at Scale – Raktim Singh
Registry governs the actors. Enterprise Agent Registry: The Missing System of Record for Autonomous AI – Raktim Singh
Runtime governs the execution. Enterprise AI Runtime: What Is Actually Running in Production (And Why It Changes Everything) – Raktim Singh
That’s “running intelligence,” not “deploying a model.”
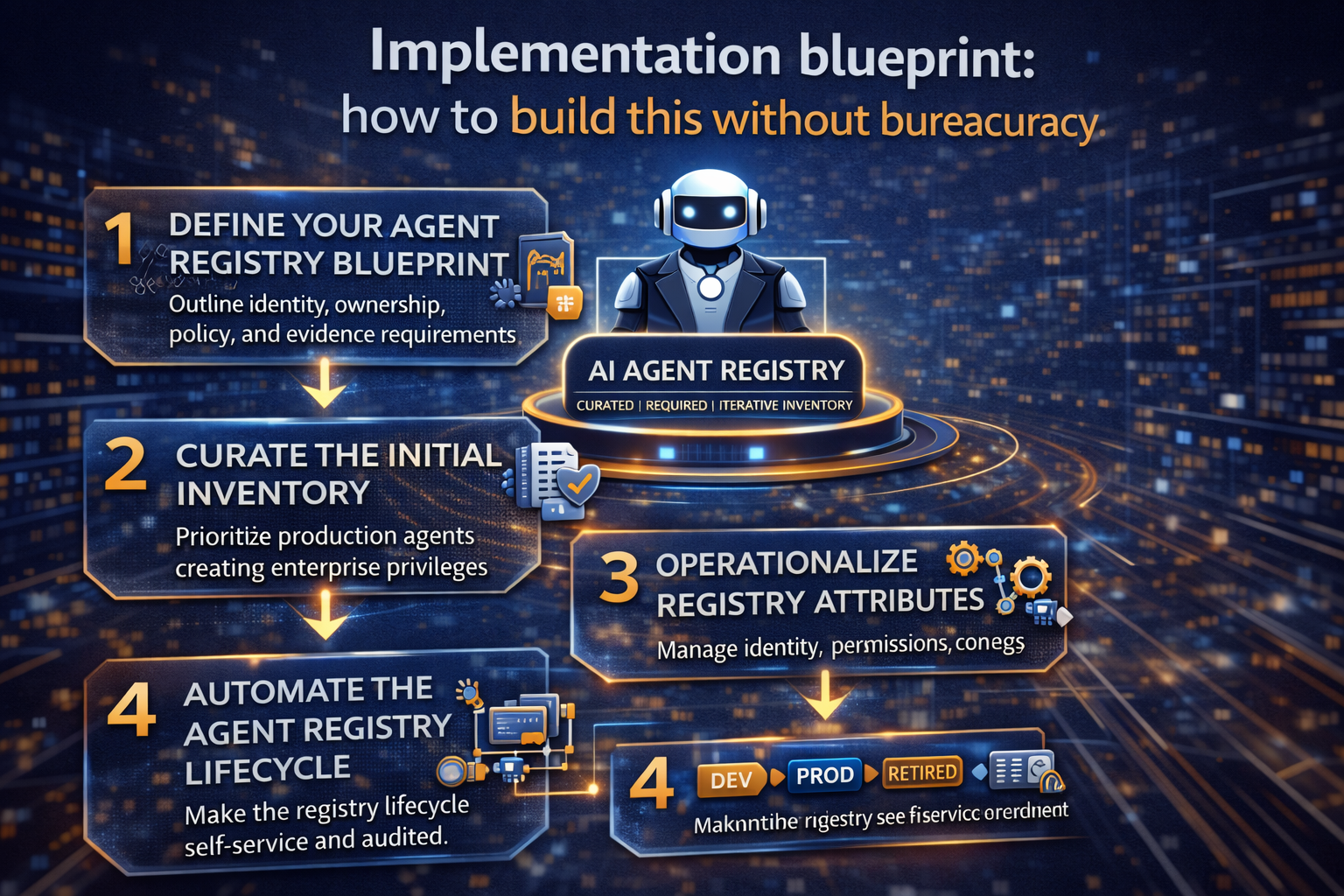
Implementation blueprint: how to build this without bureaucracy
Step 1: Introduce a production gate (fastest win)
Make a simple rule:
No agent gets production credentials unless it is registered.
This one decision instantly reduces chaos.
Step 2: Create an Agent Card schema
Define the fields (identity, owners, scope, tools, permissions, evidence, lifecycle). Keep it consistent.
Step 3: Integrate with IAM (agent identity becomes real)
Use your enterprise identity platform to issue:
- agent identities
- scoped tokens
- auditable actions
Microsoft’s approach to agent identities shows how identity platforms are designing specifically for autonomous agents and auditability. (Microsoft Learn)
Step 4: Enforce tool allow-lists and least privilege
This is the practical mitigation layer for OWASP-style GenAI risks in production deployments. (OWASP)
Step 5: Require evidence links
No evidence links = not production.
Evidence links should be automatic, not manual.
Step 6: Add expiry and re-certification
Agents should be treated like privileged integrations:
- periodic reviews
- permission recertification
- owner confirmation
This is how your enterprise avoids “autonomy debt.”
The most common anti-patterns
Anti-pattern: “Agents run under human tokens.”
Fix: enforce agent identity issuance and forbid borrowed credentials. (Microsoft Learn)
Anti-pattern: “No owner, no accountability.”
Fix: registry requires business + technical owner, plus expiry.
Anti-pattern: “Tool sprawl.”
Fix: explicit tool allow-lists; block everything else.
Anti-pattern: “We can’t audit behavior.”
Fix: registry links to logs, decision records, and incidents.
Anti-pattern: “We can’t shut it down quickly.”
Fix: identity revocation + tool blocks as first-class controls.
Glossary
Enterprise AI Agent Registry: The system of record that catalogs agent identities, owners, permissions, tools, policies, lifecycle state, and evidence links.
Agent Identity: A distinct identity representation for autonomous agents (increasingly formalized by identity platforms). (Microsoft Learn)
Workload Identity: Cryptographically verifiable identity for services/workloads across environments (SPIFFE/SPIRE is a prominent standard). (Spiffe)
Tool Allow-list: A controlled list of tools/systems the agent can call; everything else is blocked.
Least Privilege: Granting only the minimum access required to complete a task.
Revocation: The ability to stop an agent by pausing execution or revoking identity/tool access.
Evidence Links: Pointers from the registry to logs, traces, decision records, evaluations, and incident history.
FAQs
What is an Enterprise AI Agent Registry?
An Enterprise AI Agent Registry is the authoritative system of record that tracks every autonomous agent’s identity, ownership, permissions, tools, policies, lifecycle state, and audit evidence.
Is an Agent Registry the same as a model registry?
No. A model registry tracks model artifacts. An agent registry tracks autonomous actors that use models + tools to take actions.
Why do enterprises need agent identities?
Because autonomous systems must be auditable and revocable. Identity platforms are already formalizing agent identity patterns to support secure, trackable autonomy. (Microsoft Learn)
How does an Agent Registry improve security?
It enforces least privilege, restricts tool access, and enables fast revocation—directly reducing production risks highlighted by GenAI security communities. (OWASP)
What’s the fastest way to start?
Make registration a production gate: no production agent credentials unless the agent is registered with an owner, scope, tool list, and evidence links.
Enterprises won’t lose control because agents are too intelligent.
They’ll lose control because agents become unregistered actors.
If you don’t have an Agent Registry, you don’t have Enterprise AI.
You have unmanaged autonomy.

Raktim Singh is an AI and deep-tech strategist, TEDx speaker, and author focused on helping enterprises navigate the next era of intelligent systems. With experience spanning AI, fintech, quantum computing, and digital transformation, he simplifies complex technology for leaders and builds frameworks that drive responsible, scalable adoption.
